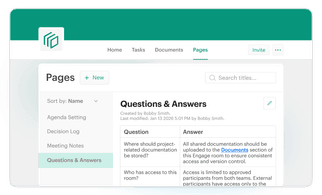
Pages in Tresorit Engage
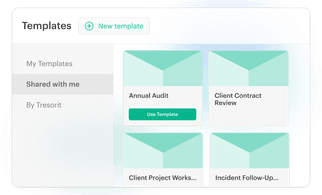
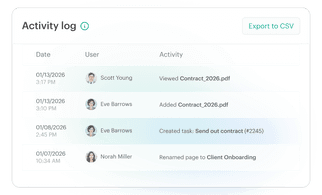
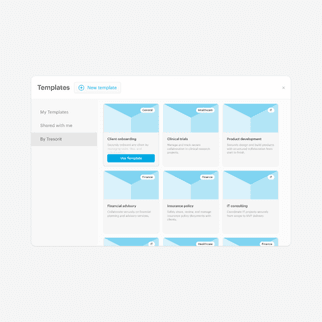
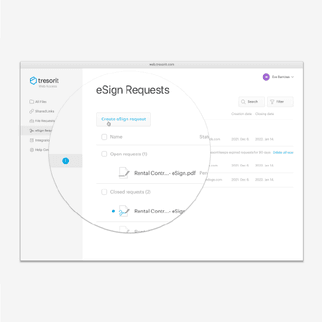
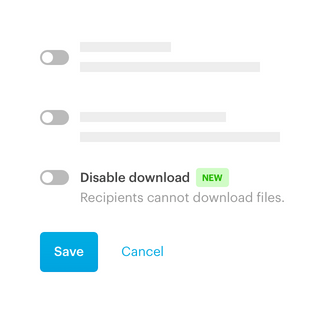
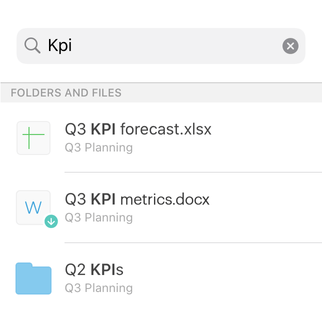
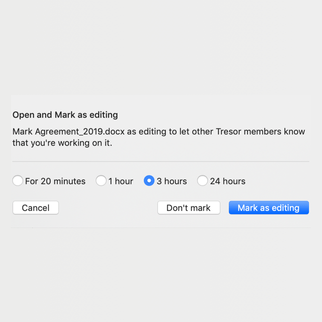
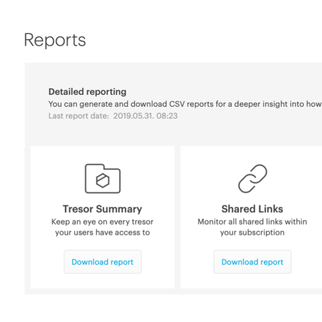
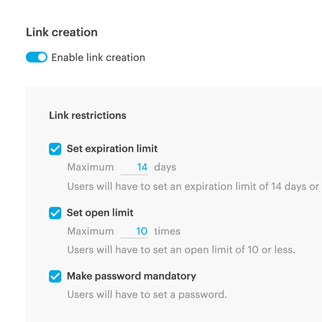
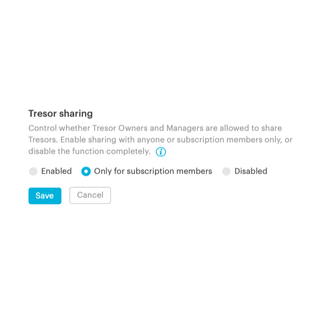
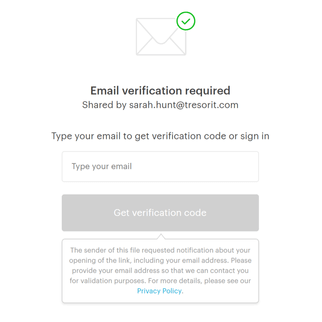
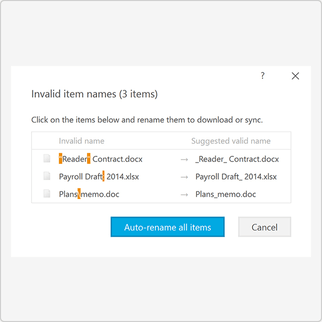
With Pages in Tresorit Engage, teams bring all relevant project information together on clearly structured pages. So critical context is easy to capture, organize, and revisit throughout the project lifecycle. Create a central knowledge and collaboration hub for meeting notes, project plans, Q&As and other key information. Instead of being scattered across tools and conversations, everything lives in one clear, centralized place, keeping teams aligned and work moving forward inside the secure Engage environment.