How to send documents securely via email: top email safety tools and tactics, explained

Email is still a major attack vector for cybercriminals – and it’s not likely to get dethroned anytime soon.
According to Verizon’s 2023 Data Breach Investigations Report, business email compromise (BEC) attacks have almost doubled since 2022 to represent more than 50% of all incidents that fall under social engineering. In these scenarios, bad actors leverage existing email threads and context to persuade recipients to perform a seemingly ordinary task.
More often than not, their efforts don’t go in vain. Based on research by the US Cybersecurity and Infrastructure Security Agency (CISA), “within the first 10 minutes of receiving a malicious email, 84% of employees took the bait by either replying with sensitive information or interacting with a spoofed link or attachment.”
Looking at these numbers, you might wonder: Just how safe are your files when you email them? Is it safe to send documents via email at all?
This concern is particularly pressing when sensitive information is at stake. In this blog post, our goal is to shed light on how to securely send documents via email, including why email security should be a top priority for businesses and what solutions are available to make sure that your confidential data remains exactly that – confidential.
Encryption: the holy grail of sending documents securely via email
A crucial safeguard when emailing confidential documents, encryption is used to convert information into an unrecognizable format, decipherable only by those with the correct decryption key. This way, sensitive data remains hidden from unauthorized individuals, even if they manage to intercept the communication. For businesses that frequently share sensitive information such as financial reports, confidential business strategies, or personal customer data over email, encryption should be integral to organizational security protocols.
The same goes for companies who operate in industries such as healthcare or financial services. These sectors are subject to strict privacy laws that prescribe how sensitive information and personal data should be handled, stored, and transmitted, facing costly fines and severe legal implications for non-compliance. Think: the Health Insurance Portability and Accountability Act (HIPAA) in the United States or the Payment Card Industry Data Security Standard (PCI DSS), a global standard created to protect cardholder account data.
What type of documents can you send over email?
File size is pretty much the only thing that limits what attachment you can and cannot send in an email. Let’s see the most common types of files that are shared this way.
- Text files: These are the simplest form of files, often with extensions such as .txt or .docx. They can be sent via email and opened with any text editor.
- PDFs: Portable Document Format files, or PDFs, are widely used due to their ability to retain the same formatting irrespective of the device or software used to open them.
- Image files: JPEG, PNG, and GIF are common types of image files that can be sent over email. They vary in terms of quality and file size.
- Audio files: MP3, MP4, WMA, FLAC, AAC, or WAV files can also be emailed, making it possible for users to share music or podcasts with varying levels of quality.
- Video files: Videos such as MP4, MOV, or AVI are larger files but may be sent via email. File size restrictions may apply depending on your email provider.
- Presentation files: Files created in PowerPoint or Keynote can be sent by email. These may contain slides with text, images, audio, and video elements.
- Spreadsheet files: Excel or CSV files can be shared via email. These typically contain cells organized in rows and columns and are used to calculate and sort data.
- Compressed files: ZIP or RAR files are used to make large files or multiple files more manageable for email transmission and take up less space when stored.
- HTML files: The backbone of web development, HTML files allow the creation of visually appealing and interactive web pages and can be sent via email.
- Executable files: .exe files or other types of software installation files may be sent via email. However, due to security risks, many email providers block these types of files.
- CAD files: Files created in computer-aided design software, like .dwg or .dxf files containing 2D or 3D data about a designed object, can be shared by email.
- Database files: Files like .sql or .mdb, used to store records in a structured format that is easily retrievable by software or web applications, can also be emailed.
The 3 best (and most secure) ways to send documents via email, explained
There are several methods to ensure the safe transmittance of files via email, with the most popular ones being password protection, email encryption, and encrypted attachments.
How to password protect an email attachment
Password protecting documents is a simple yet effective measure to ensure that only the intended recipients can access your sensitive files. Microsoft 365 applications like Word, Excel, or PowerPoint, for example, come with a built-in feature that allows you to set a password for documents. This, technically, encrypts the document with the password: when you send such a password-protected file via email, the recipient will need to enter a password to decrypt and open it. This adds a layer of security to your attachments, warranting that even if your email were intercepted, the intruder would not be able to access their contents. That said, it’s crucial that the password should be shared with the receiving party in a secure manner, preferably through another communication channel, to avoid interception.
How to email encrypted files for added safety
A key security practice to safeguard the privacy and confidentiality of email conversations, encryption converts the content of your emails into an unreadable format. This way, only authorized recipients can decipher the message with a unique decryption key. While most email service providers offer built-in encryption options, it’s important to verify and enable encryption settings for enhanced protection. Encrypted emails not only shield your attachments but also protect the sensitive information within the email body, fostering a secure communication environment. Remember: both the sender and recipient should have an encryption-capable email client to ensure seamless and secure exchange of information.
How to send secure email attachments
The third most common method to enhance email security is encrypting individual files before attaching them. Numerous software tools provide file-level encryption, requiring recipients to possess the decryption key to access file contents. This approach is especially valuable for sending sensitive documents, such as presentations or legal contracts, as it offers an extra layer of protection beyond password security.
The most basic form of encryption is Transport Layer Security (TLS), which encrypts data in transit. Web-based email services, such as Outlook and Gmail, use TLS to encrypt messages in transit being sent to the same service, explains TechTarget. If the receiving server doesn’t have TLS enabled, however, the message will not be encrypted. Plus, as TLS only encrypts the data in transit and not the email itself, it won’t prevent messages from being intercepted and read once delivered.
A more advanced way to protect email attachments is to use either Secure/Multipurpose Internet Mail Extensions (S/MIME) or Pretty Good Privacy (PGP). The two methods are identical except for two things. First, PGP uses a web of trust, while S/MIME relies on certificate authorities for trust. Second, S/MIME is often more compatible with enterprise email clients like Outlook or G Suite. It’s also worth noting that the email recipient and subject line will not be encrypted in either case.
How to send confidential documents in an email: a step-by-step guide for Tresorit users
Tresorit’s email encryption feature makes encrypting emails a hassle-free, almost intuitive process. It takes exactly one click to make sure that sensitive information gets transmitted in the most secure way possible. There’s no need for recipients to have a Tresorit account to read and reply to encrypted emails – even replies are encrypted by default. Let’s see how to securely send files via email with Tresorit.
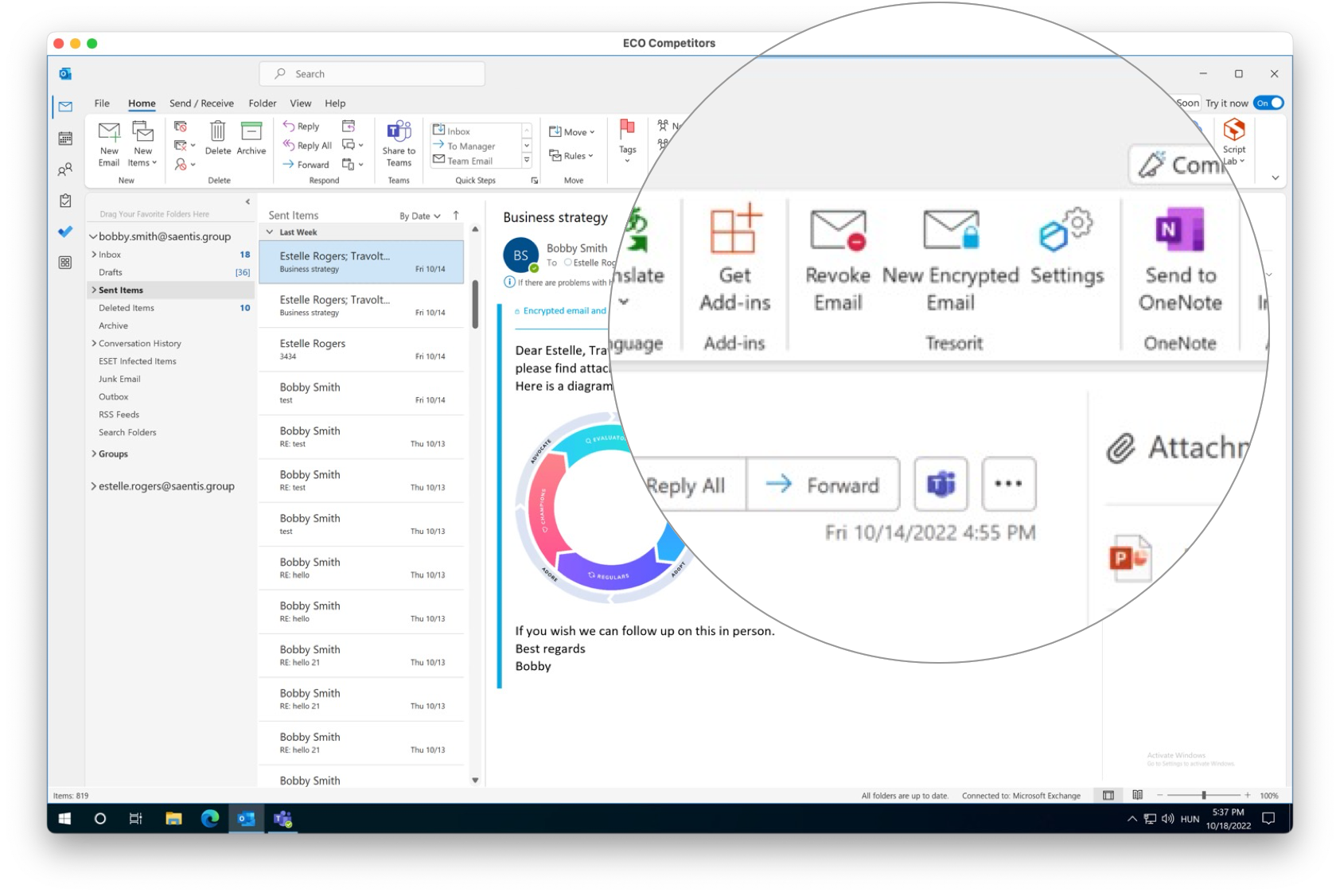
1. In Outlook for Windows, open a new email. Write your message as you usually would, adding recipients, subject, content, and attachments.
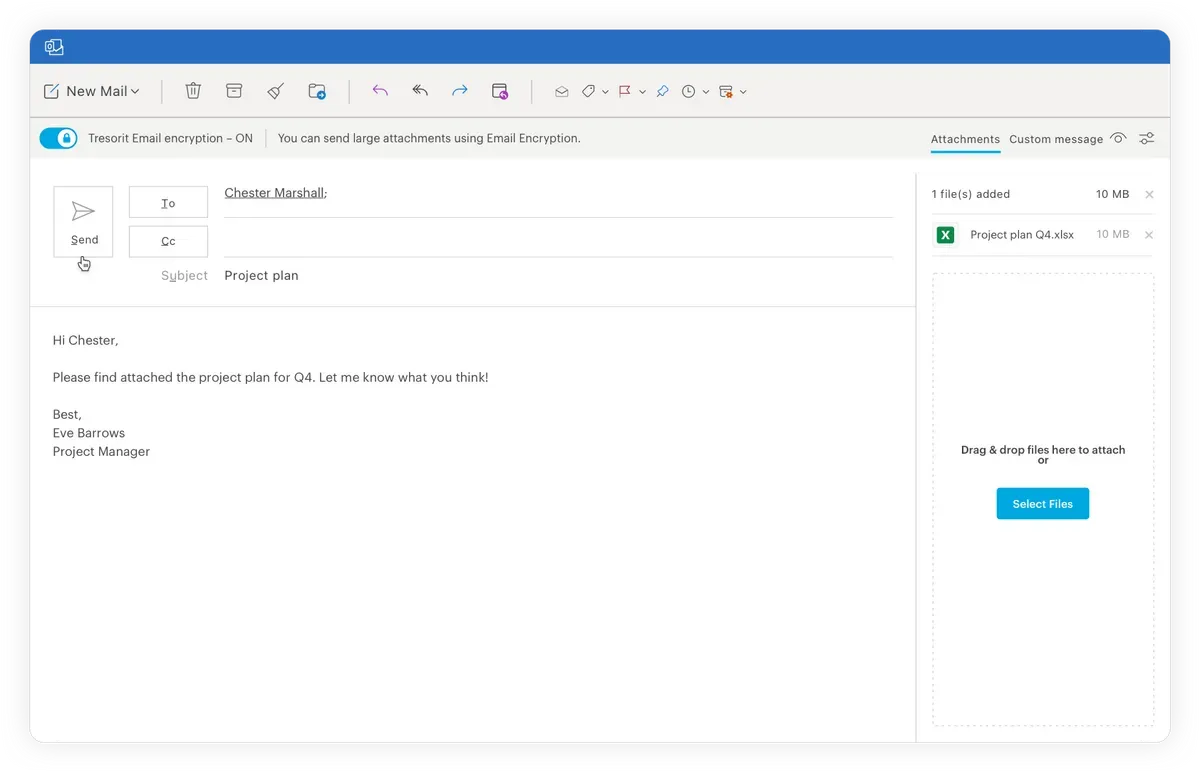
2. Before sending, toggle the Tresorit Email encryption button in the top left corner to turn on email encryption for the message. Then hit Send as normal.
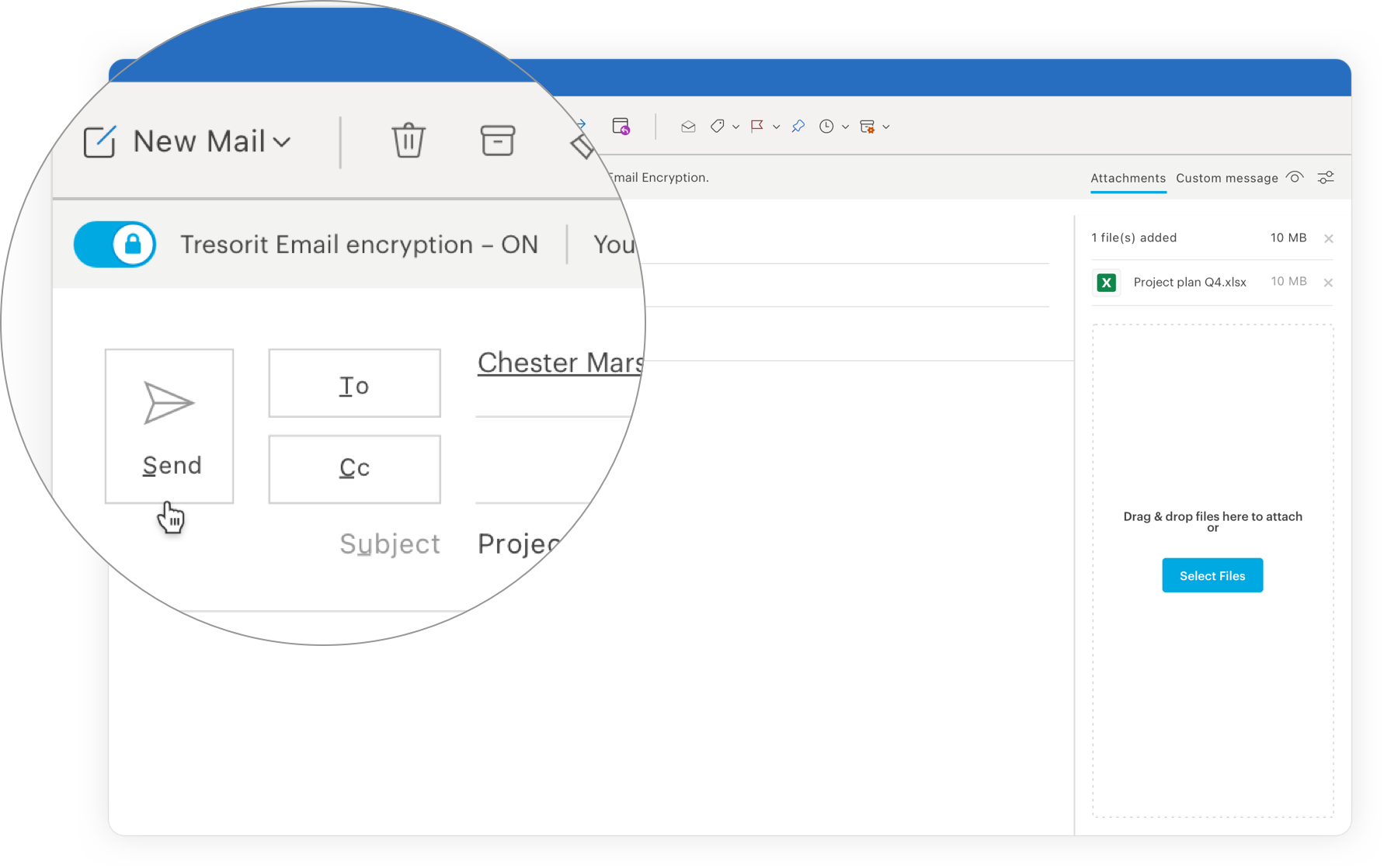
That’s it! But it does get even easier than that. Subscription administrators can minimize the risk of human error by setting rules to automatically encrypt messages based on whether the recipient is trusted or if the message contains an attachment.
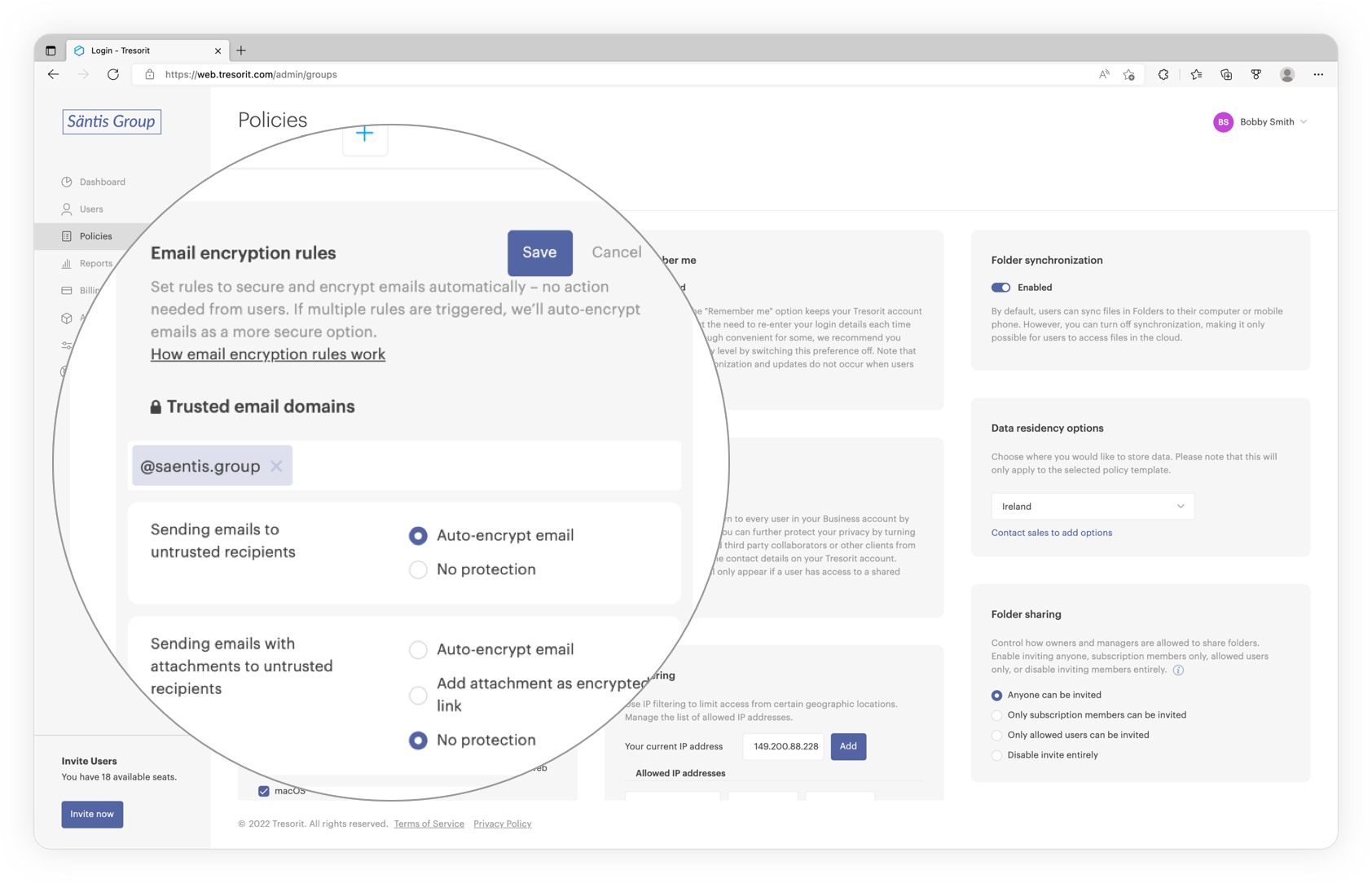
What happens after your message is sent?
If the recipient is another Tresorit email encryption user, receiving an encrypted email will be business as usual. If they click on the email in their inbox in Outlook for Windows, it decrypts automatically.
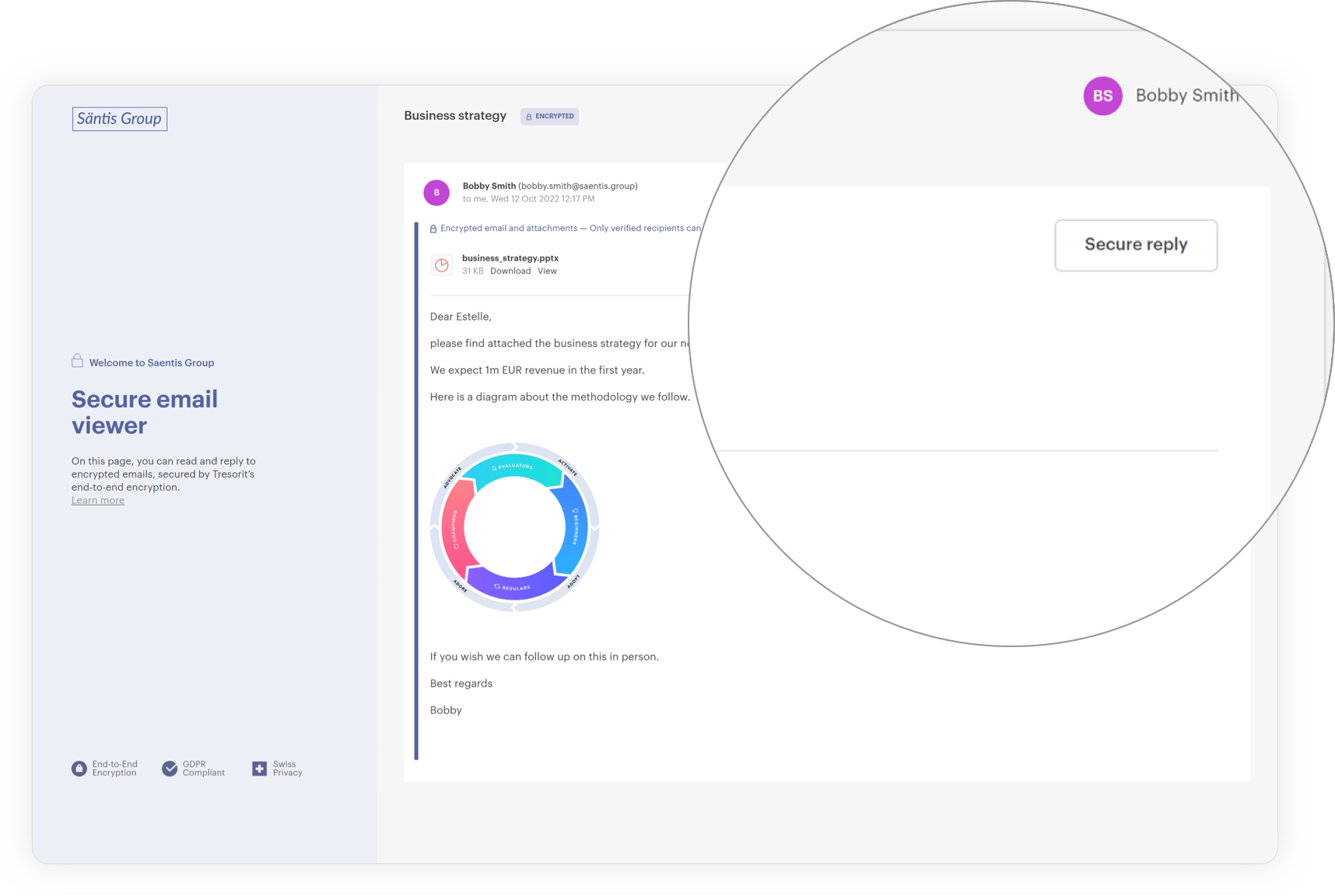
If the recipient doesn’t have a Tresorit account or uses an unsupported platform, they can access the message in-browser by opening it and clicking the Read and reply button.
Once the secure email viewer appears, they should enter their email address and verify it with the code sent to them. They can now access the secure email portal and read your message.
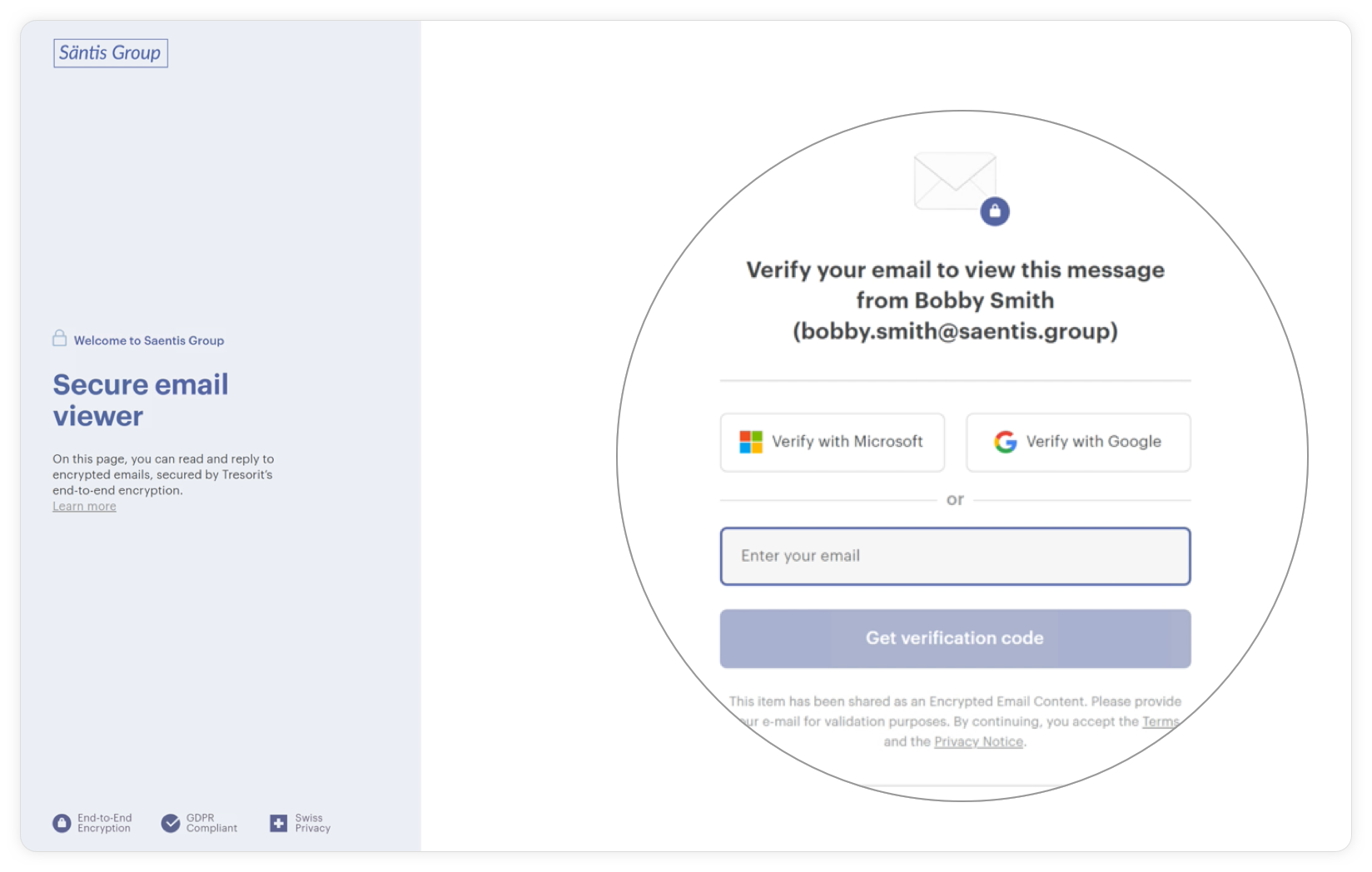
Replying to a Tresorit-encrypted message is just as simple. All the recipient has to do is click the Secure reply button, compose their message as they usually would, and hit Send.
Did your message end up in the wrong mailbox by accident? Worry not. Tresorit allows you to revoke access to sent encrypted emails with a single click to avoid data leakage.
Looking to make the most of Tresorit’s email encryption capabilities? Head to our Knowledge Base for comprehensive information and step-by-step guides on how to do just that. Ready to see Tresorit email encryption in action?






