We care about your privacy. You should too!

Tech magazine ZDNet reported this week that thousands of login credentials of the end-to-end encrypted file storage service Mega have been published online and compromised accounts have been accessed by intruders.
Current reporting points to credential stuffing rather than a breach of Mega’s systems. This refers to a practice when cybercriminals reuse login details from other data breaches and run it against multiple websites. In the case of Mega, unauthorized parties could get into user accounts as they got hold of logins from a previous breach and certain users were using the same password for their Mega account.
Therefore, it’s important to stress that it’s not Mega’s end-to-end encryption that was compromised and allowed the breach. However, there are certain security features that Mega could have provided to prevent or at least to mitigate the effect of such an incident.
Unlike Mega, Tresorit offers and encourages users to enable two-factor authentication.1 This is an extra layer of protection that can play a significant role in reducing the risk of unauthorized access in case your password gets into the wrong hands. Tresorit business users are able to enforce two-factor authentication for their team as a security policy.
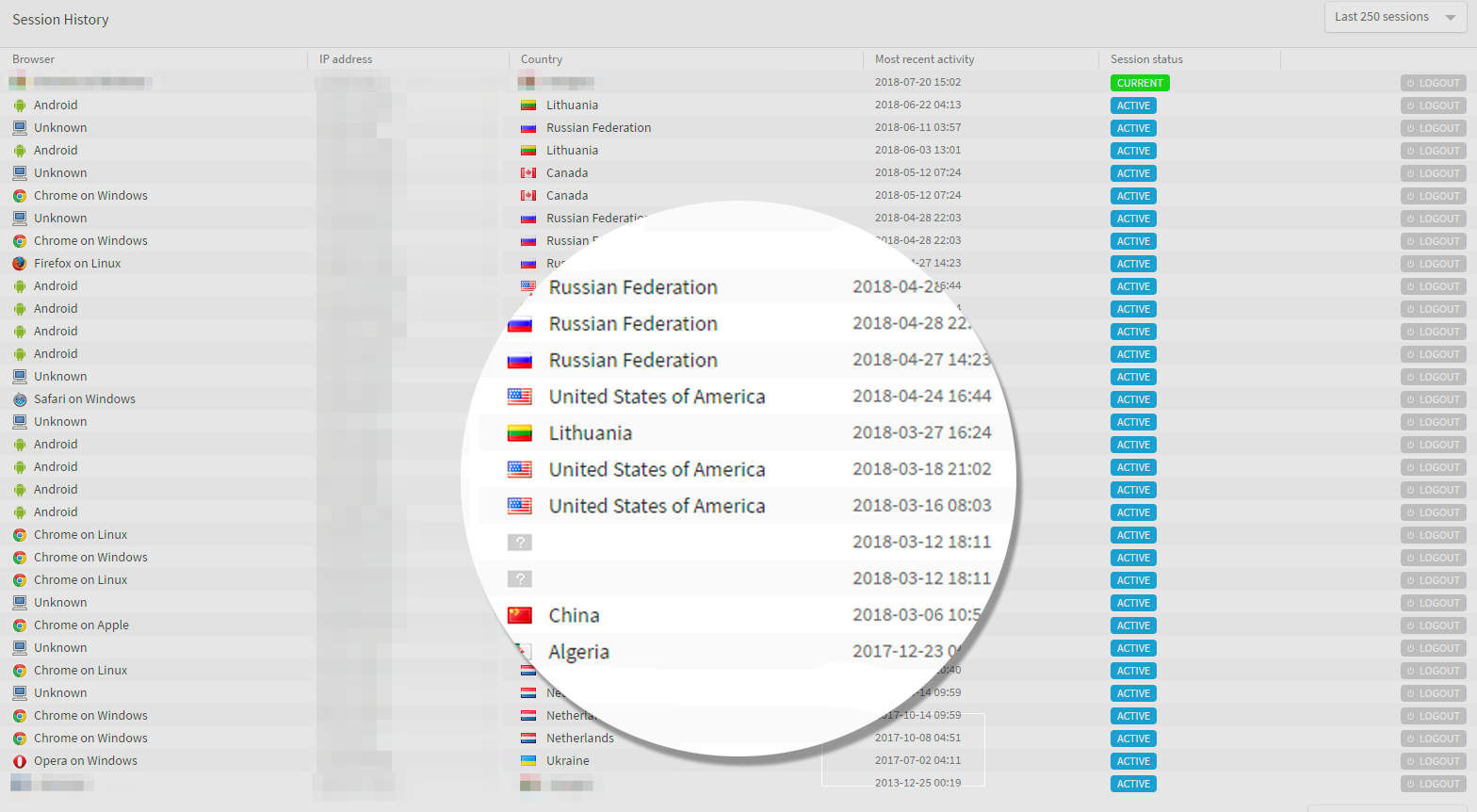
With Tresorit, admins can also activate extra security features such as limiting access to certain IP addresses (e.g. office or home) from where login is allowed. Victims of the Mega breach reported that they saw, in their session history, suspicious logins accessing their account from countries in Eastern Europe, Russia, and South America. If they had had the chance to restrict their login to certain IP addresses, they could have prevented third parties from accessing their account. With Tresorit, if this security features is enabled, even if the credentials get public, the account can only be accessed from the pre-set IP address.
Also, Mega does not send email alerts to all users about unusual sign in activities. The picture shows the session history of a Mega user. The account was opened in 2013 but the user did not log in since. As of 2017, several logins happened from different locations, devices and browsers. Yet, the user did not receive any notification about suspicious login activity.
In Tresorit, when a sign-in is detected from a new device or browser, the user receives an email with the device name, approximate location and IP address associated with the access. This is to notify the user that his/her credentials were stolen and so that he/she can immediately sign in to end the unauthorized session and change the password.
While we put several security measures at your disposal, protecting your account is your responsibility too.
Zero knowledge, end-to-end encryption is the best way to ensure the integrity and confidentiality of your data. End-to-end, or client-side encryption means that all the encryption happens on your computer. Neither your files, nor your password leaves your device unencrypted. Passwords are salted and hashed with strong industry standard algorithms before they leave your device. In case of a breach on our side, only the hashed passwords could leak and hackers could only access and read your files if they were able to reverse your password. That is why password strength is crucial.
That said, you need to have a strong password and make sure to protect it properly, otherwise you give a possibility for fraudulent actors to access your password and then your files. In case you have strong passwords, it is nearly impossible to reverse them. However, if you use a weak password, hackers have a better chance of getting into your account. Also, if you don’t follow some basic rules about password protection (for example if you use the same password for several accounts or write it down on a paper) you leave room for others to get hold of your credentials.
Let’s revisit some dos and don’ts to ensure sufficient protection for your accounts:
Take These 10 Steps Now to Reach Password Perfection
✅ create strong passwords
✅ use a password manager
✅ check if your password has already been compromised
✅ enable two-factor authentication
✅ password-protect your devices
❌ don’t use the same password for several accounts
❌ don’t store your list of passwords on your computer in plain text or on paper
❌ don’t keep a password for too long
❌don’t use easily guessed passwords (date of birth, nickname, birthdate)
❌don’t share your password with anyone
1UPDATE: Mega supports the option of two-factor authentication since October 2018.






