CMMC redefines cybersecurity in US defense industry

Planned transition to a new approach to security
Cybersecurity is constantly evolving, and for governments, this evolution is a question of national security. As new threats arise, new technologies to counter them must be researched, and at times, the guidelines and best practices connected to securing data reviewed. This is precisely what the US Department of Defense (DoD) has done with the Cybersecurity Maturity Model Certification (CMMC).
CMMC – The what, where, and why
The main goal of the CMMC is to protect Controlled Unclassified Information or CUI. In this use case, CUI refers to all data owned by the government or other entities on its behalf. As a result, it covers not only prototype development or operational security but financial or legal documentation and even infrastructure.
The CMMC was created to unify the cybersecurity standards used throughout the DoD supply chain and simplify how these are enforced and monitored. Rather than accepting self-certification, it will require checks to be carried out by third-party auditors to prove compliance. Rolled out through a trial between 2021 and 2025, it will become the base of operating within the DoD supply chain in the long term.
What are the implications of not complying with CMMC guidelines?
The CMMC employs a tiered certification solution. Companies will be evaluated on a scale of five levels. Those at Level 1 display “Basic Cyber Hygiene,” while those at Level 5 demonstrate “Advanced, progressive cybersecurity.” The highest levels of certification will require companies to create systems and processes capable of countering advanced persistent threats.
However, as part of its phased implementation, no companies are expected to achieve Level 5 before 2025. In the long term, Level 3 will be the base level of compliance required for projects within the DoD supply chain. Those who are non-compliant or suffer data breaches will be barred from working on DoD projects.
How does Tresorit support compliance with CMMC?
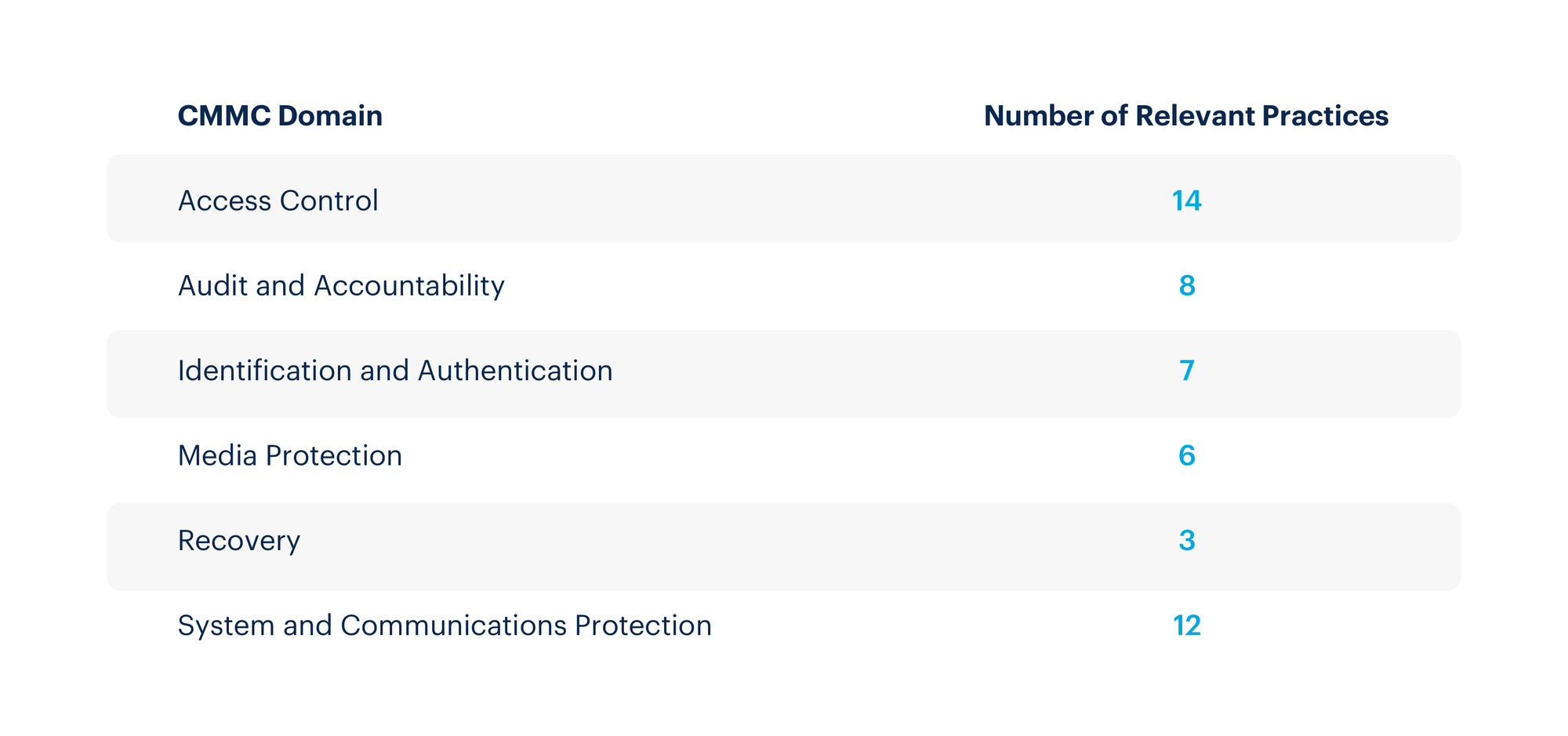
The CMMC divides its guidelines into 17 domains ranging from Access control to Audit and accountability, Recovery, and System and information integrity.
Zero-knowledge end-to-end encrypted (E2EE) cloud storage supported by state-of-the-art security features provided by Tresorit can help you achieve CMMC certification on multiple fronts:
- Secure Controlled Unclassified Information: All data stored on Tresorit is protected by military-grade encryption. Zero-knowledge multi-factor authorization ensures that not even passwords leave devices when logging in. Only a salted hash reaches our servers.
- Client-side integrity protection: Tresorit guarantees that a file’s content cannot be modified without your knowledge. Clients apply cryptographic authentication to all encrypted data. The key is only known to the user’s client and those they share the file with.
- Managing access rights and permissions: Role-based user rights for managing subscription policies and various access permissions allow granular control over who is authorized to access files.
- Manage users and monitor file activity: The admin dashboard provides easy access and centralized storage for detailed activity reports, user management, authorized devices, team-based policies, and essential user statistics.
- Data encrypted on mobile devices: As all data stored in our cloud is only ever decrypted at the client-side, Tresorit ensures that data remains secure even when accessed from mobile devices.
- Easy recovery from multiple encrypted backups: Robust version tracking allows previous versions of files to be restored at any time. Secure, redundant backups on multiple servers ensure that no data is ever lost.
The complexity of CMMC means major preparations will be needed from affected companies. Tresorit can help defense contractors overcome several hurdles through E2EE storage for any sensitive information.
Begin preparations for CMMC today with Tresorit.






