Secure and easy business cloud storage, file sharing, & collaboration
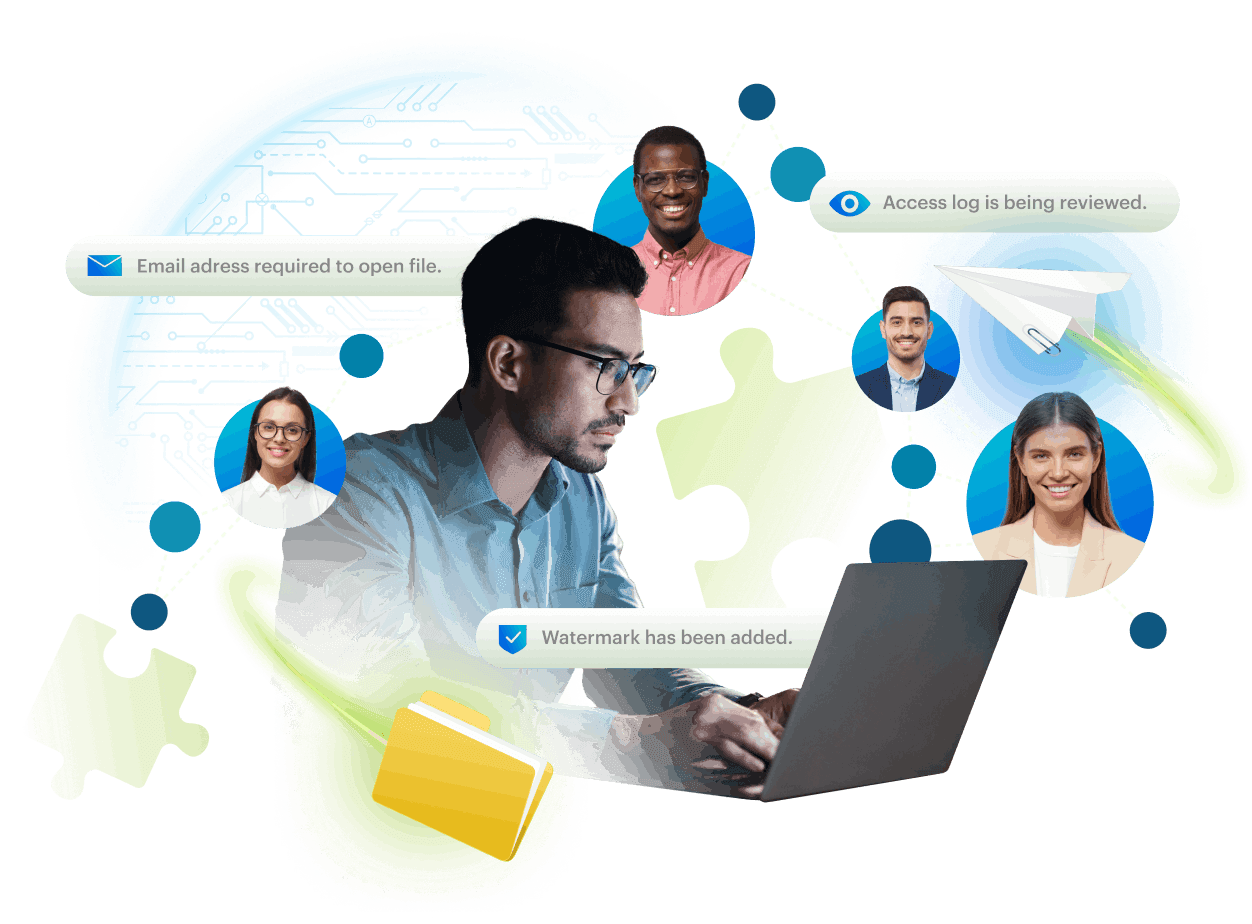
Securing business file sharing & storage has never been more critical
With workforces worldwide increasingly mobile with work from home policies, and with consultants, partners, and customers handling thousands of private documents daily – often stored or shared through insecure public clouds – ensuring your organization meets security, privacy, and compliance standards is urgent and paramount.

Choosing the right corporate file sharing & collaboration platform
Nowadays it is far too easy for hackers to gain access to your confidential files as they’re stored and shared in insecure public clouds. Also it’s too easy for unaware employees to make security mistakes or forget to revoke accesses when sharing files with external parties.
Protecting your company’s confidential information from unauthorized access and breaches.
Ensuring compliance with your most significant privacy, security, and regulatory requirements.
Maintaining ease of collaboration between employees – and external partners and cross borders.
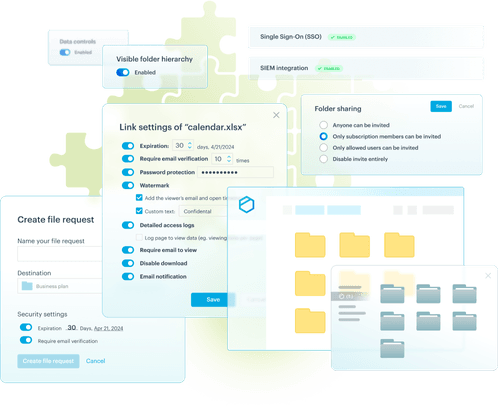
Introducing Tresorit’s secure business file sharing and cloud solutions
End-to-end encryption – With zero-knowledge built in, Tresorit encrypts all your files and emails. Meaning that no hacker, unauthorized person, and not even Tresorit can gain access.
Secure external file sharing – Benefit from the most advanced external corporate file sharing controls available on the market. Set passwords, open limits, and much more. Get email notifications when files are accessed and monitor complete activity logs.
Share, sync, and collaborate from anywhere – Tresorit is available across mobile, desktop, and web platforms, so your employees and external customers or partners can access the information they need without sacrificing security or privacy.
Integrates with tools and platforms your company already uses – From Microsoft 365 to MacOS to Gmail, and from your Active Directory to your SSO, & SIEM, Tresorit integrates with them all.
Leverage a multi-certified and consistently audited platform – From ISO27001 to the Swiss Digital Trust certifications, from HIPAA to TISAX, Tresorit solutions are audited several times a year so the security commitments we claim are not just words, but facts.
Compared to other services like Dropbox, Tresorit’s solution is much safer. Compared to manual encryption, it’s less hassle. And compared to other online services, it offers a much better overall package.
Dr. Tobias Zimmermann
Research fellow, The Cardiovascular Research Institute Basel
The importance of secure business file sharing and document storage in healthcare
Try Tresorit free for 14 days
Share, sync, and collaborate securely with Tresorit’s corporate file sharing and cloud solutions.
What you get with Tresorit’s business cloud storage, sharing and collaboration Platform
Secure cloud storage
Import, store, and organize your files inside Tresorit's end-to-end encrypted cloud environment with ease. Ensure only those authorized can access your most sensitive assets – from documents to videos to images.
Secure file sharing
Tresorit provides top-tier external file sharing security features including email encryption. These include multiple authentication methods, link expirations, and access limits – ensuring maximum protection at all times.
Sophisticated controls
Empowering admins with total control over user management, granular permissions while offering comprehensive activity logging and audit trails. Admins also have the ability to disable and erase local syncs on devices.
Custom Brand and Domain
Your company deserves to use your corporate brand, colors and logo in Tresorit or with our encrypted emails. Including the use of your own URL domain: Tresorit can be customized to your unique needs.
Regulatory compliance
WithTresorit, you’re always in line with local, national, and international data privacy and security regulations, including GDPR, ISO27001, TISAX, HIPAA, Swiss Digital Trust, Common Criteria and more.
Multiple integrations
From Microsoft Teams to Azure Sentinel SIEMor EntraID/AD, to Gmail, Outlook, Okta and beyond. Tresorit integrates with them all out-of-the-box to enhance your organization’s security and privacy at every touchpoint.