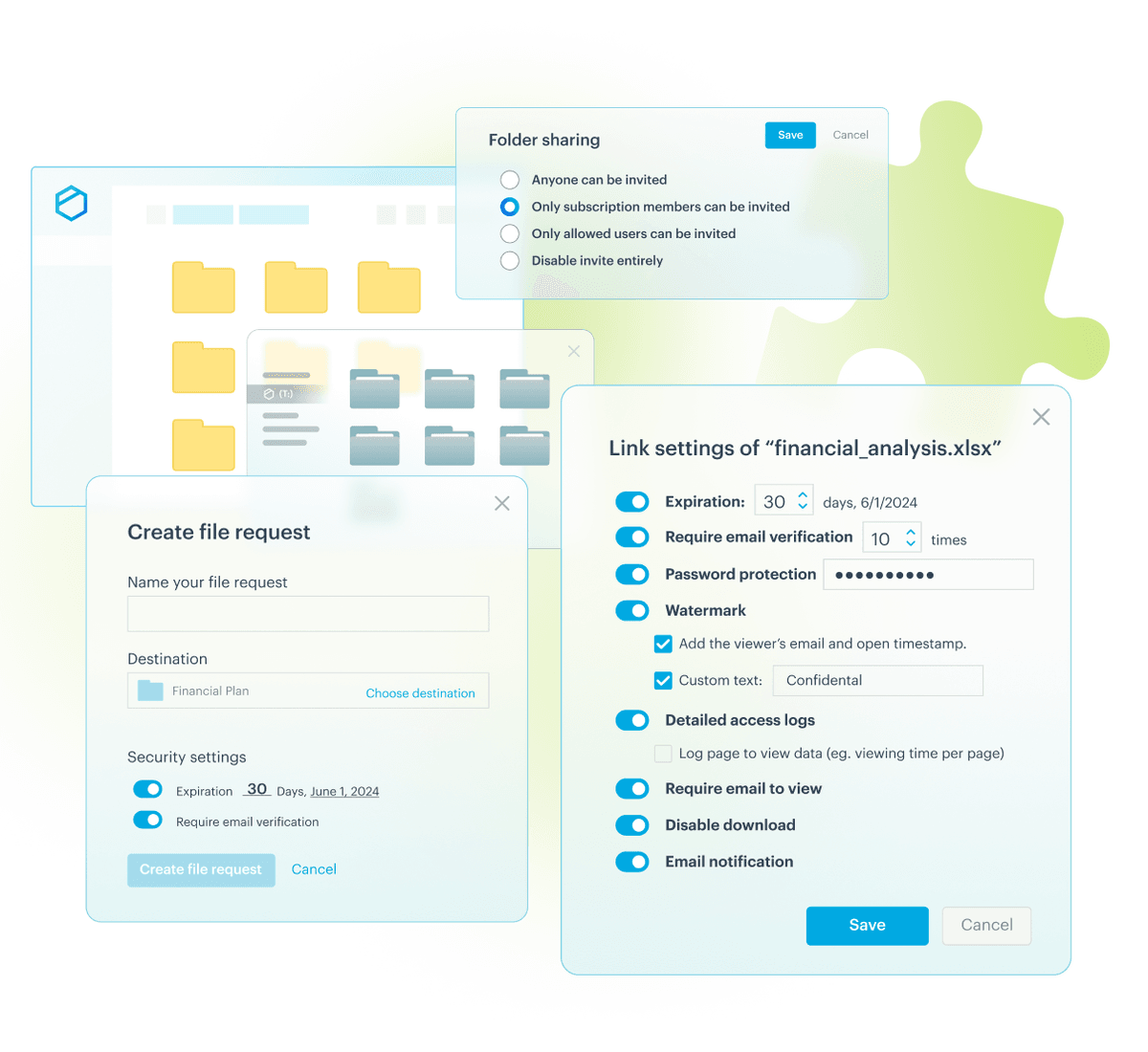
Efficiently share sensitive financial documents with one secure platform
- Instant value with a preconfigured, intuitive solution
- Seamless client collaboration, no registration required
- Security by design for risk-free transactions
Try for free![]() Start a 14-day free trial
Start a 14-day free trial
Request a demo![]() See Tresorit in action
See Tresorit in action

Trusted by 11,000+ organizations worldwide
Your Tresorit values for financial processes

Swiss Made Privacy
With Tresorit’s client-side encryption & Swiss data protection practices, you can securely exchange bank statements, tax filings, and other sensitive financial documents.
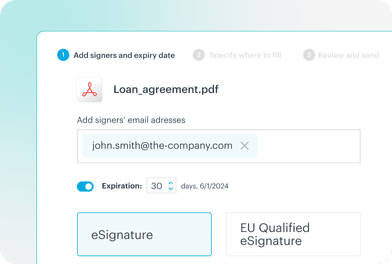
eSignatures included
freeOptimize contract lifecycles, account openings & loan origination with integrated eSignatures. Stay secure and compliant – even with rigorous European regulations.

Out-of-the-box productivity
Deliver immediate value to your customers and bring services faster to the market – no training, no account registration required.
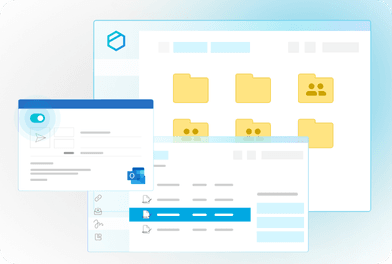
All-in-one cost-effective solution
Facilitate friction-free interactions with a single affordable platform. Protect sensitive client documents, such as investment reviews, insurance analysis & tax planning.

Industry regulations and standards
Reduce regulatory risks & insurance costs while meeting strict financial services standards – GDPR, FINRA, Bafin, MaRisk, ISO 27001, and beyond.
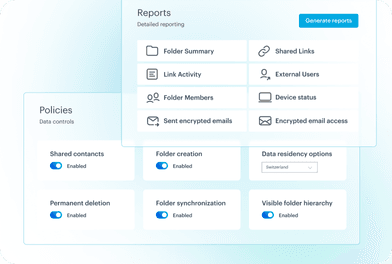
Visibility and control
Spend more time with your clients and less time preparing for financial audits - with an overview dashboard, granular controls & reporting.
Service excellence for your finance document workflows
Take action now
Try for free![]() Start a 14-day free trial
Start a 14-day free trial
Request a demo![]() See Tresorit in action
See Tresorit in action
Customer success stories
Read our eBook to learn more about:

- The fundamentals of encryption
- The strengths and weaknesses of different encryption forms
- And why you should encrypt information in the first place
Find out more
Take action now
Try for free![]() Start a 14-day free trial
Start a 14-day free trial
Request a demo![]() See Tresorit in action
See Tresorit in action