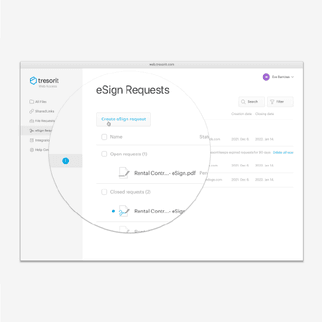
EU qualified electronic signatures for high-value documents
In addition to eSignatures for everyday signing, extend Tresorit to the signing of your mission-critical documents with EU-wide recognized qualified electronic signatures - the equivalent to handwritten signatures. Tresorit integrates with Evrotrust to help you shield them with the combination of end-to-end encryption & certified identity verification. Enjoy seamless remote signing while transacting across the EU in a compliant & risk-free way.